- 01 Aug 2023
- 6 Minutes to read
- Print
- DarkLight
Secure Edge Basics
- Updated on 01 Aug 2023
- 6 Minutes to read
- Print
- DarkLight
Read this section to gain a basic understanding of View Secure Edge software and web service. If you’re already familiar with Secure Edge and want to get right into setting up, go to Provisioning and Launching iNodes.
Secure Edge Overview
The View Secure Edge software and web-based service is a network infrastructure for managing industrial IoT (IIoT). Components participating in the infrastructure include private networks, application networks in the cloud, Secure Edge iNodes, iNode networks, network security policies, and services. You manage these components through Secure Edge Portal.
There are three types of Secure Edge iNodes:
- Edge iNodes, the physical Secure Edge network elements located at the edge of your private network. Edge iNodes connect to your IIoT devices. In most cases, you receive your Edge iNodes directly from Secure Edge. Secure Edge supports use of the following hardware for Edge iNodes:
- Dell Edge Gateway 5000
- Lanner NCA-1510D
- Lanner NCA-1510A
- Supermicro SYS-E50-9AP
- Advantech UTX-3115
- Lanner LEC-7230M
- Adlink MXE-210 Series
- Virtual iNodes, the Secure Edge network elements located in the cloud. These connect to your application network, which consists of the applications you use for your business, test and development, and data analytics. The Virtual iNodes connect your applications through Edge iNodes to your IIoT devices.
- In a VMware environment, you can also use Virtual Edge iNodes. Virtual Edge iNodes are Secure Edge network elements that are VMware instances located at the edge of your private network.
The following figure illustrates the components in a network infrastructure supported by Secure Edge.
.png)
Secure Edge Portal for Management
In this section, learn the basics about what you can do with the Secure Edge Portal.
You access the Secure Edge Portal by logging into your company’s Secure Edge account using the login and password you’ve received from Secure Edge.
Logging into the Secure Edge Portal and Changing Your Password
If you are a new user, when your Secure Edge Portal account is set up, you’ll receive an email asking you to verify your email address. Once you’ve verified your email address, you can log into the Secure Edge Portal using the credentials we sent you. You’ll be prompted to change your password the first time you login.
To login, follow these steps:
- Type <yourcompany>.secureedge.view.com into your browser, replacing <yourcompany> with your company’s name.
- Enter the login and password.
- Select Login.
If you need to change your Secure Edge password, follow these steps:
- From the bottom of the Secure Edge Portal left menu, select My Account (the person icon) > My Profile.
- Select Change Password. Enter your current password, then enter your new password twice.
- Secure Edge Portal logs you out and prompts you to login again with your new password.
You’ll be prompted to change your password every 90 days.
Passwords must contain 12 to 100 characters, including at least:
- One uppercase alphabetical character A-Z
- One lowercase alphabetical character a-z
- One number 0-9
- One special character from the set !@#$&*
You can’t use the same phrase as your email address for your password. In addition, your new password can’t be the same as your last password or similar to your last three passwords.
- You must use the email address associated with your Secure Edge Portal account in the reset process.
- You must have already verified your email address to reset your password through the reset link. If you haven’t verified your email address, you’ll have to contact Secure Edge Support at [email protected] to reset your password for you.
Using the Secure Edge Portal
The initial view of the Secure Edge Portal is a customizable Dashboard with an overview of the status of the network infrastructure it supports. It includes information about iNodes, networks, organizations, services, and users.
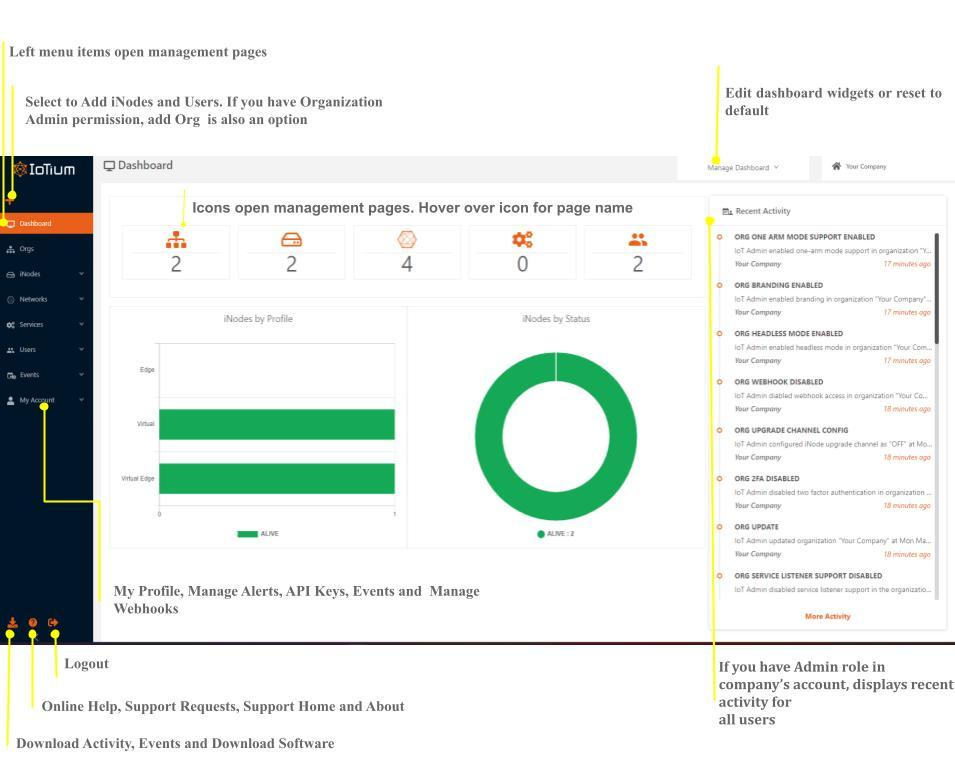 Figure 2 Secure Edge Portal Dashboard
Figure 2 Secure Edge Portal DashboardThe Secure Edge Portal left menu, or the icons on the Dashboard, open the management pages, which are used for monitoring and managing the Secure Edge Organization, iNodes, Networks, Services, and Users:
- Orgs — With Secure Edge, the organization represents the company using Secure Edge. If you have Organization Admin permission, adding Org appears as an option.
- Find information about managing Orgs and child organizations in Managing an Organization.
- iNodes:
- All iNodes — Find information about iNode status, profile (type of iNode), remote networks, and services. See all iNodes or type an iNode name into Filter iNode to select a specific iNode or a set. Select the name of an iNode to drill down. You’ll find system information, data interface traffic, and details on networks, services, interfaces, and events. System info has a down arrow that expands to display more information, including iNode uptime. Select Manage iNode to view or edit the iNode.
- Serial Numbers — Displays serial numbers of iNodes that haven’t been configured yet.
Find information about managing iNodes in Provisioning and Launching iNodes.
- Networks:
- All Networks — Find information about all networks or type a network name into Filter networks by name to highlight a specific network or a set. The Networks page includes network name, iNode name, and associated remote networks.
- Find View Network or Edit Network pages by hovering over the three-vertical-dot icon at the end of the network row, then selecting the icon for the operation you want. These pages have detailed information about network addressing, CIDR and internal reserved IP address range, and security, including custom and aggregated security policy.
- Custom Security Policy - Hover over the icons to the right of the network name to view, edit, or delete custom security policies for communications between networks.
Find information about networks and security in: - Connecting Networks
- Provisioning and Launching iNodes
- Security Policy
- Services:
- All Services — Services are representations of your applications running on an Edge iNode. You use the Services tabs to add services and to view status of services running on the Edge iNodes.
- Service Secrets — Secrets are secure objects that store sensitive data needed by containers in the service. In the Service Secrets page, you can specify and manage service secrets and volumes (directories) containing secrets.
Find more information about services in Edge Services.
- Users:
- All Users — Find information and manage users, including email addresses and assigned roles. Icons give access to edit and reset password, view sessions, and delete the user.
- All Roles — Find information about user roles and manage them. Icons give access to edit, delete, and view role information.
- My Profile — Find information about the current user’s My Profile page, including their details for Manage Alerts, Manage Webhooks and API key information.
Find more information about users and roles in below section.
User Roles with Secure Edge Portal
User roles and the permissions associated with them regulate operations users can perform on using Secure Edge software and web services. By default, the Secure Edge Portal has two permission levels represented by the roles: Admin and Read Only.
In general, the Admin role enables ability to add, edit, or delete operations. The Read Only role enables viewing of operations.
You can assign discrete roles to users based upon their responsibilities for different aspects of Secure Edge management, including Network, Org, Role, Service, User. You can also create custom roles.
Edge iNodes
In most cases, you receive your Edge iNodes directly from Secure Edge. Secure Edge supports use of the following hardware devices for Edge iNodes:
- Dell Edge Gateway 5000
- Lanner NCA-1510D
- Lanner NCA-1510A
- Supermicro SYS-E50-9AP
- Advantech UTX-3115
- Lanner LEC-7230M
- Adlink MXE-210 Series
iNode Command-Line Interface
You can use the iNode command-line interface (CLI) for a limited set of functions, including setting a static IP address for an iNode uplink interface, connecting the Edge iNode uplink using mobile broadband or Wi-Fi, or configuring an iNode to use a proxy server. See Appendix A for more information on these operations.

